Welcome to totatca.com. In the previous article, we successfully carried out the installation process of the GLPI system together. However, after completing the installation, in addition to the warning Web server root directory configuration is not safe as it permits access to non-public files. You may have encountered another noteworthy warning on the homepage PHP directive “session.cookie_httponly” should be set to “on” to prevent client-side script to access cookie values as shown below.
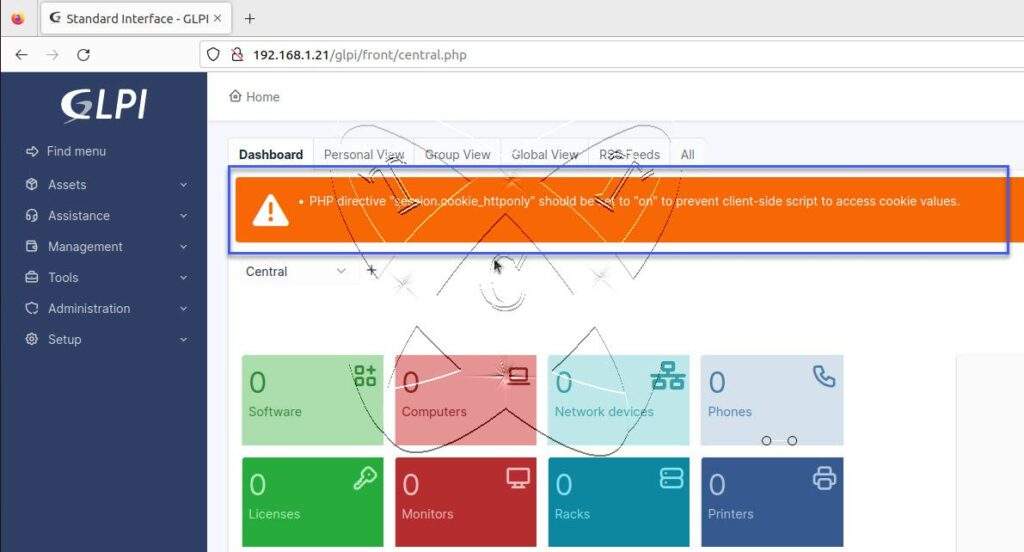
Don’t worry, in this article, we will explore detailed solutions to eliminate this warning and ensure that your GLPI system is deployed safely and efficiently. Let’s get started right away.
Read more
- How to Install GLPI 10 on Ubuntu 22.04 | 20.04 | 18.04 LTS
- How to Install and Configure GLPI 10 on CentOS | CentOS Stream | RockyLinux | AlmaLinux | RHEL
- How to Upgrade GLPI to Latest version on Ubuntu/Debian
- How to Synchronize Users from Active Directory to GLPI
- How to Install and Configure phpMyAdmin on Ubuntu with Apache
Fix Warning
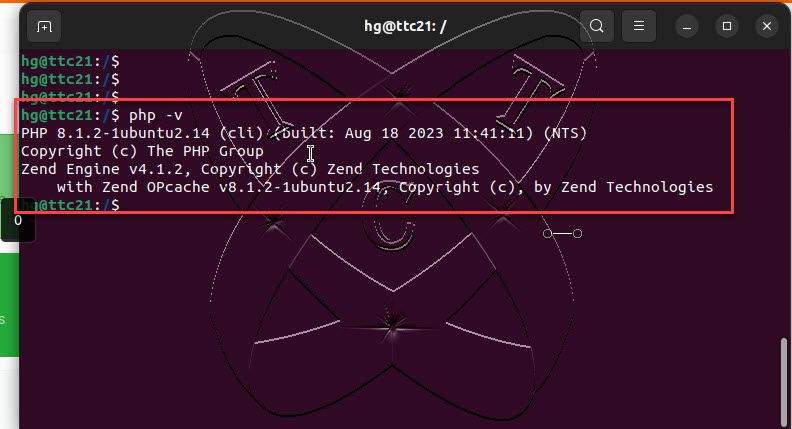
First, check the PHP version installed on your system with the following command:
php -v
As in this article, from the output result, my PHP version is 8.1.
After determining the PHP version, we open the configuration file php.ini for editing with the following command:
sudo vim /etc/php/8.1/apache2/php.ini
Note: replace 8.1 with your previously determined PHP version.
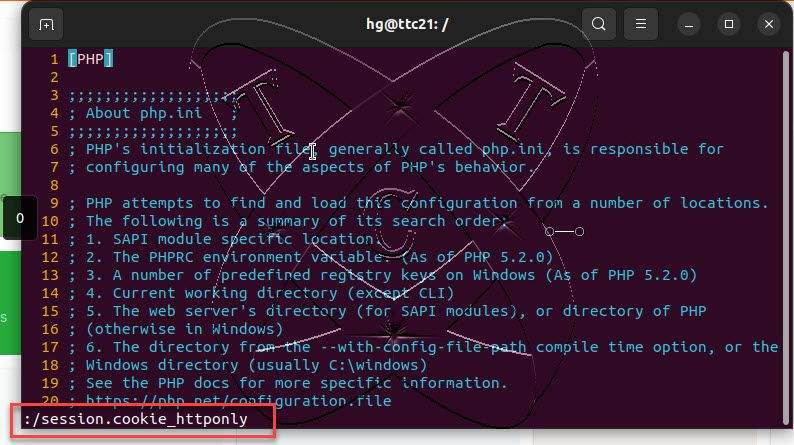
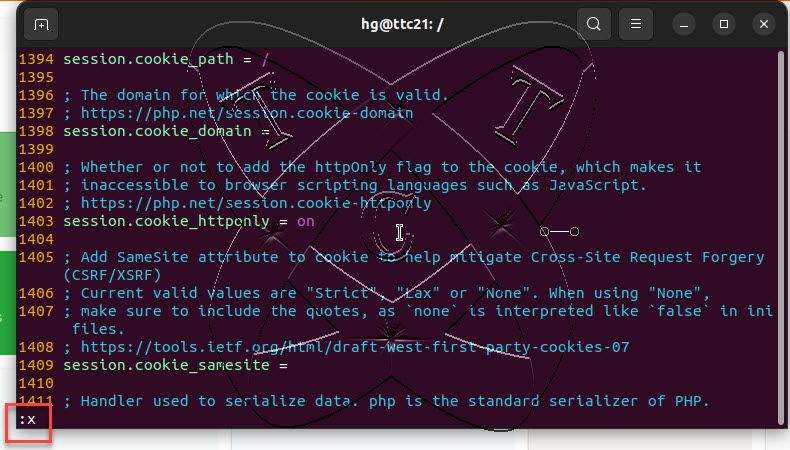
The vim window is open, press Esc and enter the command :/session.cookie-httponly and then hit Enter to navigate to the setting of session.cookie-httponly.
At the line session.cookie-httponly, press the i key to switch to the edit mode, then set the value of session.cookie-httponly to on as shown below:
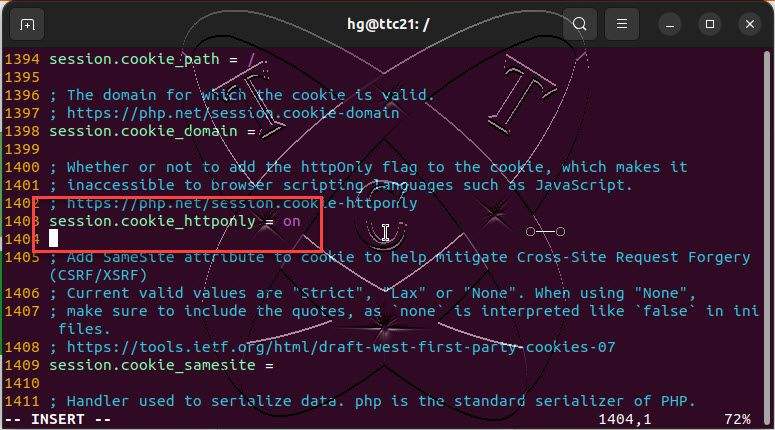
After finishing, save and exit the file by pressing Esc, entering the command :x, and then pressing Enter.
Restart the web server service for the changes to take effect.
sudo systemctl restart apache2
Finally, return to the GLPI homepage, refresh the webpage by pressing the F5 key, and you will see that the warning has been addressed:
There you have it, we have successfully disabled the warning PHP directive “session.cookie_httponly” should be set to “on” to prevent client-side script to access cookie values. Wishing you success, and don’t forget to subscribe to my YouTube channel.